Continuous improvement consists of learning from events to adjust action plans. Threats and risks change rapidly. However, past disasters are valuable lessons for preparing for the future.

The last 20 years have been marked by disasters of all kinds. These events provide feedback and areas for improvement in preparation. Consider your own past incidents, such as computer outages or cyber attacks. Did you use these events to improve and adjust your preparation?
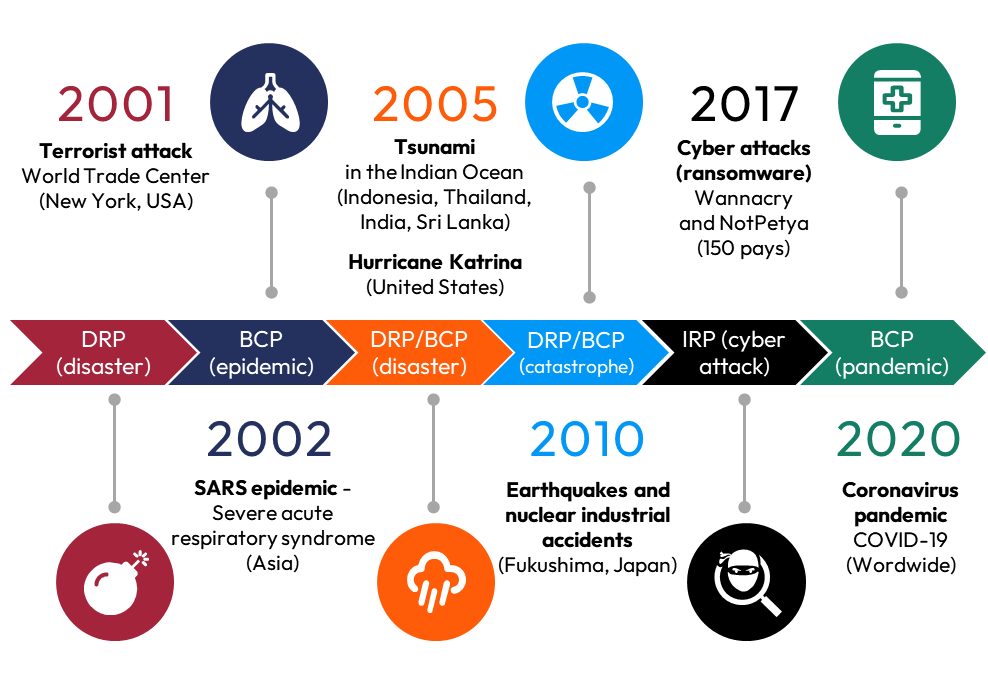
Natural disasters
The December 2004 tsunami is the biggest disaster in Indonesia’s history. This event, which devastated 800 km of coastline northwest of Sumatra, had repercussions for the entire world. Alert systems have been put in place or reinforced, as is the case in New Zealand or Japan. Any organisation that has critical infrastructure or resources in the concerned areas must now consider this risk.
When you analyze disaster scenarios, consider each of your sites and datacentre regarding their exposure to natural risks (flooding, forest fires, tsunamis, earthquakes, hurricanes, ice storms).
The devastating hurricane Katrina that hit the southwestern United States in August 2005 is instructive. Several key elements must be taken into account since this disaster. Prolonged power outages affect information systems, especially if they continue beyond what was anticipated. Without reserve batteries or enough diesel for generators, it’s impossible to access data and applications. When several areas are affected, it is not possible to intervene everywhere at the same time and the alternate sites are also affected. Finally, communication outages are a major obstacle to locating and coordinating teams.
Since the Katrina disaster, the location of a disaster recovery site is of utmost importance. The distance of 100 miles (160 kilometers) between your primary and secondary datacenter is a minimum.
Malicious acts
The terrorist attack of September 11, 2001 is probably the most appalling malicious event in modern history. The hijacking of resources (planes) against infrastructure (Pentagon, office towers) is a modus operandi found in other contexts. In some cyber attack scenarios computer systems are diverted against the target (ex. DDoS). Essentially, September 11 (9/11) will have reinforced the needs for large-scale surveillance (borders, aviation security, controls).
You should set up minimal detection systems and alerts to monitor your environment. In particular, suspicious use of your own resources or IT administration tools should be closely monitored.
Cyber attacks
The large-scale Wannacry cyber attack in May 2017 paralyzed more than 230,000 computers in 150 countries, affecting the British health agency (NHS). Since then, many variants and similar procedures have appeared. Wannacry was based on exploiting a vulnerability and self-spreading (worms). Nowadays, ransomware attacks are perpetrated by humans (organized cybercriminal groups). However, the impact is the same: inability to access the data, sometimes irreversibly. From a certain point of view, the consequences for a company’s processes are like a disaster: a general and prolonged interruption.
Years after the Wannacry and NotPetya campaigns, ransomwares are still very much around. Basic security measures have changed little. At a minimum, you should set up protected backups, quickly deploy security patches, implement strong authentication, and build an incident response plan.
Pandemics
The SARS and especially Coronavirus pandemics have considerably increased the need for IT tools (remote work, online sales, dematerialization). The dependence of companies on their information and communication systems is now increased. The resulting digital transformation will also have changed crime. With the reduction of physical contact, cybercrime has diversified and increased sharply.
Following the pandemic, many companies have modernized their information systems. Maintain an optimal level of readiness, ensuring the resilience of your systems. In particular, in a post-pandemic situation, make the extra mile to replace or decommission obsolete or unsupported systems.