We are dependent on our smartphones, wether we like it or not. They perform several essential functions in everyday life: security, travel, communication, payment. If one morning your phone fails to start, is stolen, or mysteriously disappears, what would you do?
I will guide you through 4 steps and 5 key actions to ensure that you are fully prepared.
Our phones, tablets and smart watches assist us on a daily basis. Can you imagine spending a day without your phone? Beyond the actions that will be more difficult to perform, you could be victim of identity theft. It’s easy to protect your phone, prepare yourself and learn to spend a day without your phone if the worst happens.
Step 1: Identify how you use your phone
Our phones include many features. We know they are useful, but we forget to have a contingency plan for their loss. Before starting, you need to know the applications you use on a daily basis. You need to understand how you use your phone.
There are two techniques depending on your self-measurement preferences:
The paper method: every time you take your device, you write down the task you are doing. You can also replay your day and remember everything you did with your device.
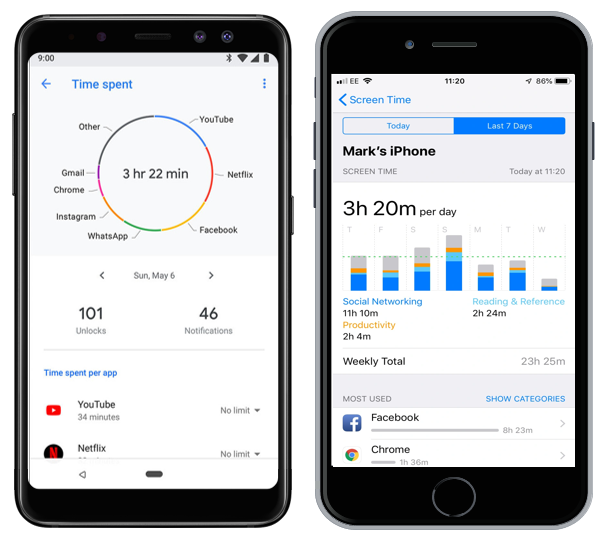
The digital method: use the wellness app on your phone or the one you have installed. It will tell you how much time you spent on each application. You will have to determine what you have done with each application.
To help you, here is a list of the main functions of your smartphone:
- Communication (phone, text messages, emails, messaging applications)
- Time management (calendar, timer, time measurement application)
- Personal organization (to-do list, GPS, calculator, weather, scanner, notes)
- Identity and access (strong authentication, remote control)
- Purchase of goods and services (food, transport, bank)
- Specific search (web browser, social networks, dedicated application)
- Entertainment (social networks, web, games, videos, photos, music)
Step 2: Secure your device
Set up basic security
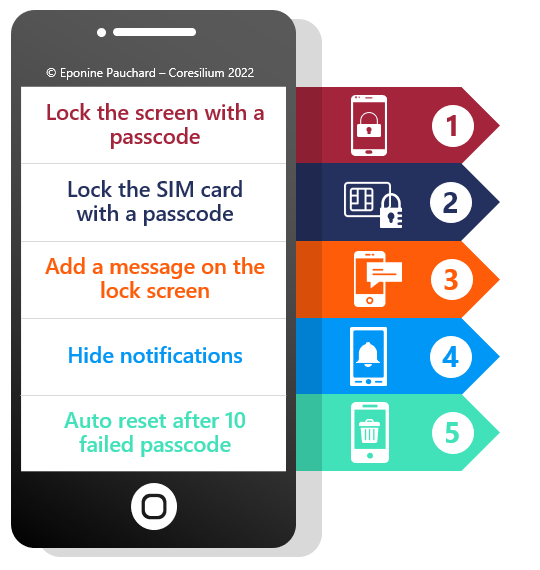
The first thing to do is to use the basic security features of your device. Here are the 5 main actions to protect your phone in case of loss or theft.
- Activate the automatic screen lock with a passcode. The passcode is more difficult to remember than a pattern.
- Protect your SIM card with a passcode. If someone gets their hands on your phone, they can put the SIM card in another device and receive the strong authentication messages for you. To confirm that this is the case, restart your phone. You should have two screens requesting a password or PIN code to unlock your device: one for the phone and one for the SIM card.
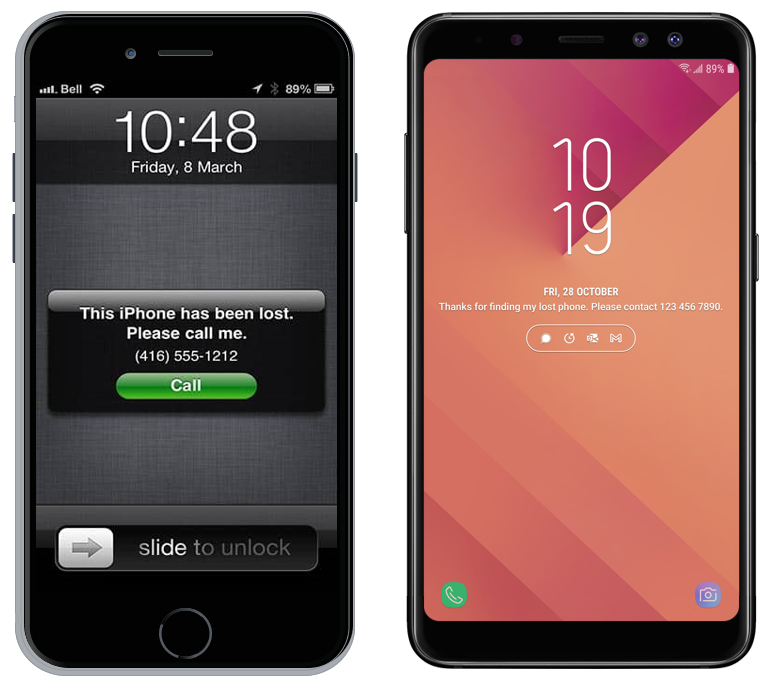
- On Android, use the “owner info” feature to display a message on the lock screen. Include the phone number or email of a family member or friend who could respond. You could have a lost phone address for the whole family for example. Most people will try to return the device to its owner. On iOS, you’ll be able to send a message from iCloud, after marking your phone as “lost”, in the locate-my-phone feature below.
- Hide critical app notifications on the lock screen. If someone finds your device, you don’t want them to be able to read your emails or bank notifications. What notifications do you need to see on the lock screen?
- If you don’t have a child or pet playing with your device, consider enabling the feature that automatically deletes data from your phone after 10 failed passcodes on iOS and the number you set on Android.
These actions are available in the security menu of your phone settings. Search for lock screen, lock screen display, owner info. Review all settings and make sure they meet your needs.
Check your online account
Once the phone setup is complete, switch to the computer and do the following two checks:
- Activate and test the locate-my-phone feature of your device. Go to the site (link for each platform below), try to locate your device and make it ring. On Android, you have to activate the remote security. On iOS, it is automatic, from here you can send a message with a number to contact you.
- Make sure your storage space is not full. With both Apple and Google, when your storage space is full, automatic backups of your data and applications are no longer made. You can check the storage status in your Google and iCloud account. Delete your photos and videos, clean up your emails to make sure backups are done properly. This page also displays the date of the last backup.
Other actions
If you want to further increase your level of protection, here are some additional actions to take:
- Buy an anti-spy screen, which will prevent anyone from seeing what you are doing on your device and especially your unlock code.
- Turn off Bluetooth and wifi if you’re not using them, but keep the phone connected to 3, 4, or 5G so you can locate it.
- Log out of sites after making an online payment, as your payment information is stored, reducing the risk if someone accesses your device.
Step 3: Find alternatives and test them!
Obviously, no one wants to activate an emergency plan. But if you have prepared then you will know what to do. For each of the applications you use every day, you should find at least one alternative solution.
I propose a few of them, for the functions that I consider the most critical. It’s up to you to put them in place. If it’s obvious that an alarm clock can replace your phone’s alarm. You still need to have one, with charged batteries and know how to program it.
Communication
You can configure most communication applications such as Facebook Messenger, WhatsApp, and Signal to be used on your computer. Simply scan a QR code on the computer to synchronize contacts. However, some of them require your phone to be connected to work. Turn off your phone to test if you can reach your main contacts.
In the same way, you can access your e-mail messages from your computer. Ask your employer for the address to access your external messages and add it to your favorites. Then, go to each of your mailboxes from your computer.
If you have multi-factor authentication enabled, you may not be able to access your messages if your phone is missing. Some solutions store authentication for a few days or weeks. Use your computer from time to time to ensure that communication applications are always connected.
The telephone will probably be the most difficult function to replace. If you no longer have a residential line, you can use another family member’s phone. The phone booths have totally disappeared, so you have to find someone who will lend you their phone to make your calls.
Identity and access
If you follow our advice, you have strong authentication in place wherever it is available. And most importantly, you have chosen several options to authenticate yourself. In this case, you will be able to receive your authentication codes on an email address or on your phone. But if your email accounts are disconnected from your computer, you are blocked.
Take the time to print out backup codes, so you can access your account even if you no longer have a phone and computer connected. Google and iCloud have different procedures. Do not write your email address or password on the printed codes and keep them at home.
Step 4: I lost access to my phone, what do I do?
If you have taken the time to read this article, and implement the recommendations, you can breathe easy. The first step is to understand the situation.
I have my phone, but it is unusable
You can still take it in for repair, but you’ll need a new device. You can proceed to the last step.
I don’t know where my phone is
In this case, go to your computer and launch your phone’s location feature for Android or iOS. Hopefully, it’s close by and you’ll hear it ringing.
If you find it’s stolen, you can mark it as “lost” on iOS or remotely lock it on Android. A code will prevent access to your data. This will give you time to contact the authorities and decide what to do. If the device is not recoverable, you can remotely erase it. The device will be more difficult to resell.
I got my new phone!
Congratulations, it will take you about half a day to reinstall your device. Be patient.
I suggest you start by turning on the phone, logging into your Google or Apple account and doing all the system updates.
Then review all security settings to activate them. You can then go to the list of applications and decide from the Play Store or App Store which ones you want to install.
The data should sync automatically as you log into the apps. This step may take some time. Make sure you have a good Internet connection.
Finally, you will need to reinstate all the strong authentications you had installed.