You are much more likely to fall victim to ransomware than experiencing physical destruction of your servers. Discover ways to adjust your backup strategies to address new threats. In addition to resilient backups, I will explain effective methods for preparing your organisation to face a major cyberattack.

The 321 backup rule was invented many years ago by a professional photographer. This strategy has proven to be very effective when the main risk is physical or accidental destruction of data. In this context, there were no ransomware-type cyberattacks. Nowadays, this approach has become inadequate.
A reinforced 321 backup rule
In the event of a major cyber attack, assume that your entire infrastructure will be unavailable: identity servers, file servers, business applications, databases, network services, password managers, etc. Your backup servers will also be directly affected. They will have to be reinstalled before the infrastructure can be restored!
I suggest strengthening the 321 backup rule by incorporating measures for resilience against cyberattacks.
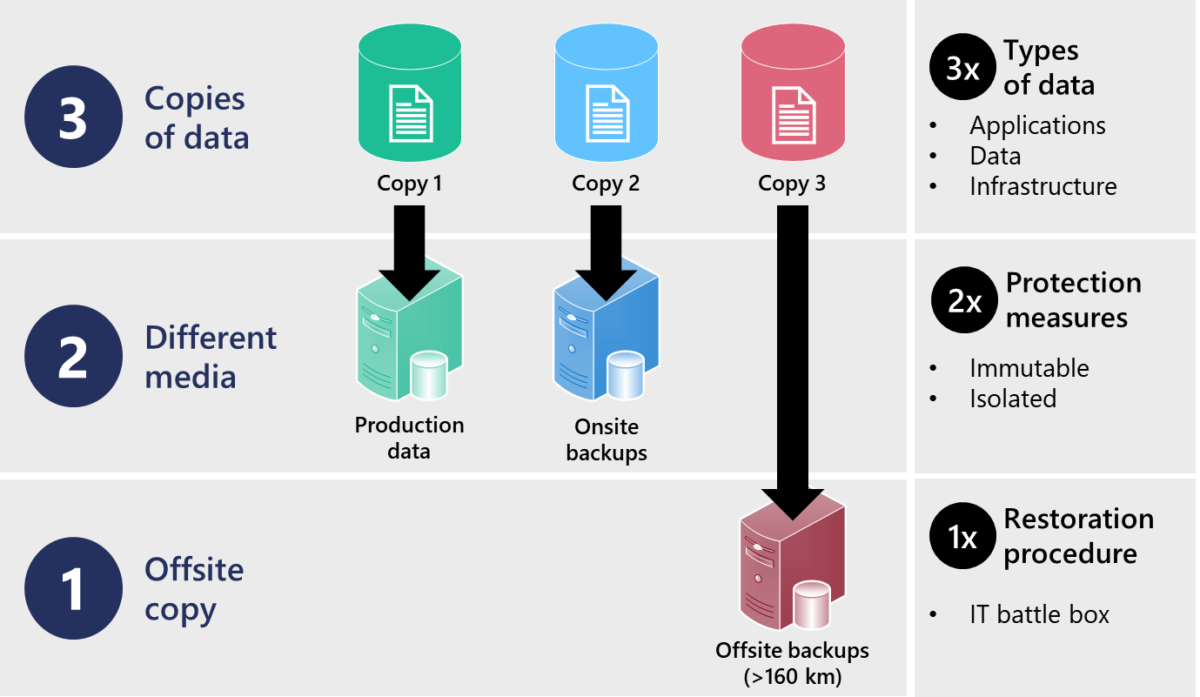
Here’s how you should improve the 321 backup principle:
- Three copies of data (production, local and external) must include all three types of data. These three types of data are: business applications, databases or files, and finally the infrastructure servers themselves.
- Two different media (disks, tapes, removable media, etc.) must be secured by two different protective measures. The media must be indestructible (read-only, immutable) and isolated (access restriction, separate network, stored in a safe).
- An outsourced copy should also include one computer emergency kit. This kit contains a detailed restoration procedure. It is advisable to utilise a paper format or an external medium that is not connected to your information system.
4 steps to a stronger 321 backup
I suggest implementing your resilient backup strategy in 4 simple steps.
1. Back up all your critical systems
Consider all systems and data, as well as the basic infrastructure. Include identity and access management services (Active Directory, LDAP, etc.). In addition, don’t forget the essential networking servers (DNS, DHCP, etc.).
In the event of a major cyberattack, restoring your primary software server is not enough. Your users won’t be able to connect to servers if the necessary infrastructure is not in place.
2. Protect your backups from destruction
Your backups must survive a motivated cybercriminal group that will seek to delete them manually. An attacker who has obtained administrator access will use it to destroy your backups.
In most cyber attacks, humans are behind the machines. They simply use your own administration tools against you. During the attack, they scan your networks, discover the software or connected backup media. Afterward, they will attempt to deleta all data backup prior to launching the final attack.
The best protection is immutable storage. This technology ensures that backups cannot be deleted without physical intervention or on-site access. If it is not feasible, restricting access to the backup server is a good alternative. Place your backups on a separate network with dedicated user accounts that are not synchronized with your infrastructure.
3. Guarantee access to your backups in case of emergency
You need to be able to access your backups, even if your infrastructure is compromised or inaccessible. To begin, it’s crucial to be able to completely reinstall a backup server from scratch. To accomplish this task, ensure that you have all necessary tools at your disposal: software, IP addresses or media locations, encryption keys, and passwords.
I recommend preparing an off-line computer emergency kit that will contain the essentials to rebuild a computer system from the ground up. This emergency kit should contain, at least, the following: paper documentation, USB keys, dedicated laptops, basic software, strong authentication keys, etc. You can also store your emergency kit in a dedicated Cloud storage not connected to your infrastructure.
The idea of having an “emergency kit” or “survival kit” is not new. However, you can adapt this concept to your IT systems to prepare for a potential destructive cyberattack scenario. Do you have all the essentials to get back on track in case of disaster?
4. Document a reliable and tested restoration process
Your team must be ready to restore all IT functions and data in the correct order to ensure the systems’ integrity and full functionality. Take the time to document everything. A global recovery of your computer systems is very different from a small-scale data restoration. Rebuilding your entire infrastructure is a complex task, especially without a functioning IT network to rely on.
Maersk was the victim of a ransomware attack that compromised all of its computers and servers at all of its locations. Following a power outage in Ghana, the local Active Directory server was spared from the cyber attack. This single existing copy of the domain controller played a crucial role in the recovery of the group’s IT systems.
Simulation testing is essential. Start by testing the recovery of your Active Directory, DNS and DHCP services. Obviously, use your computer emergency kit in a test network. Then, run additional small simulations, every 3 to 6 months, restoring critical systems, databases and applications. If you find that some applications are dependent on others to work, fix and improve your recovery process. Each time, update your computer emergency kit according to your experiences and difficulties.
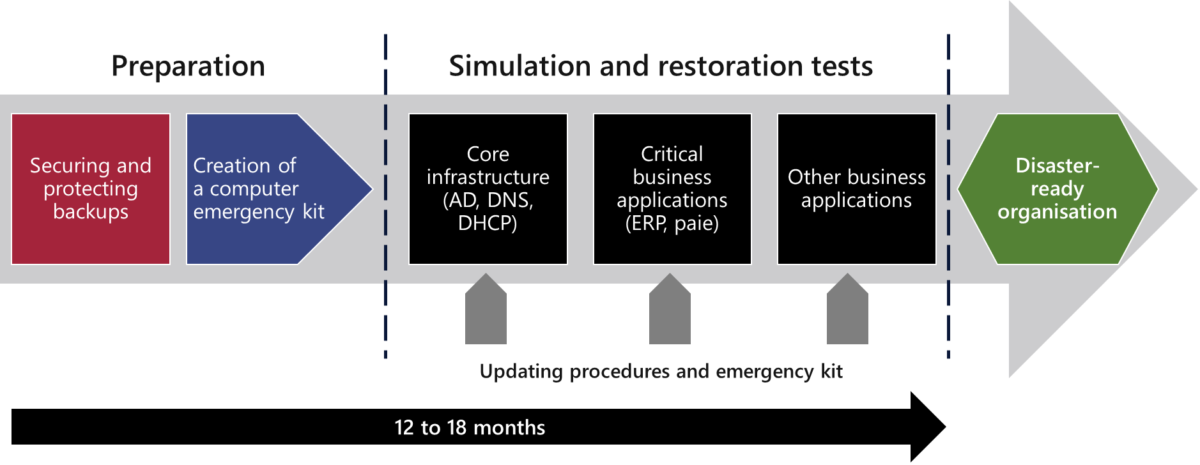
In addition to keeping your teams ready, trained and experienced, you will be able to communicate with management. In this way, they will gain clear visibility into how long it will actually take to recover from a major cyberattack. The management team will then be able to better understand the risk, the impacts and decide on funding priorities to best prepare the organization.