In cybersecurity, if you don’t know where to start, focus on what’s most valuable (the famous “crown jewels”). To unlock the full potential of your intangible assets, you need to identify and protect them. It sounds simple. However, companies do not always know the value of their intangible assets. In many cases, they are more a source of risk than opportunity.

I had the pleasure of attending the conference of Paul Adams, CEO of EverEdge Global. The topic was the financial valuation of intangible assets. I found the approach both engaging and meaningful. Intangible assets play a crucial role in a company’s operations and overall value proposition. However, these “intangible” assets pose a growing cybersecurity threat and are often poorly understood.
Intangible assets are risky
Physical (or tangible) assets such as servers, computers, routers, and other IT equipment seem very valuable. In reality, they have little value compared to intangible assets. Nowadays, a powerful laptop, a fast Wi-Fi router, or the latest graphics tablet are no longer a significant source of competitive advantage for companies. If this equipment is stolen or destroyed, it can be replaced quickly and at a reduced cost.
Intangible assets bring tremendous value to an organisation, but they also carry a significant level of risk. Data, intellectual property, customer information and specific knowledge are essential. In fact, intangible assets represent up to 90% of the value of most companies.
Unfortunately, intangible assets are highly exposed to cybersecurity risks. It is even the major source of risk for modern companies. Protecting them from cyber threats is not just a matter of compliance or best practices. This is a strategic priority for any competitive and sustainable organization.
Protect what is most valuable first
Your secret sauce, know-how, reputation, brand, relationships and processes are all intangible assets stored in digital form. Recognise that this information, stored on your computer systems, is very valuable. You must both identify and make it difficult to destroy or steal these assets.
Protecting digital assets is key to the success and longevity of your business. However, before you can protect these assets, you need to understand what they are and the risks they face.
The first step is to identify and understand your intangible assets. You can’t protect what you don’t know exists. In addition, you may be unknowingly accepting significant risks if you are not aware of the value of the intangible assets you own.
Get to know your intangible assets
The first step is to identify all your intangible assets stored in digital form. Once you have a complete list, perform a ranking based on their confidentiality, integrity and availability requirements.
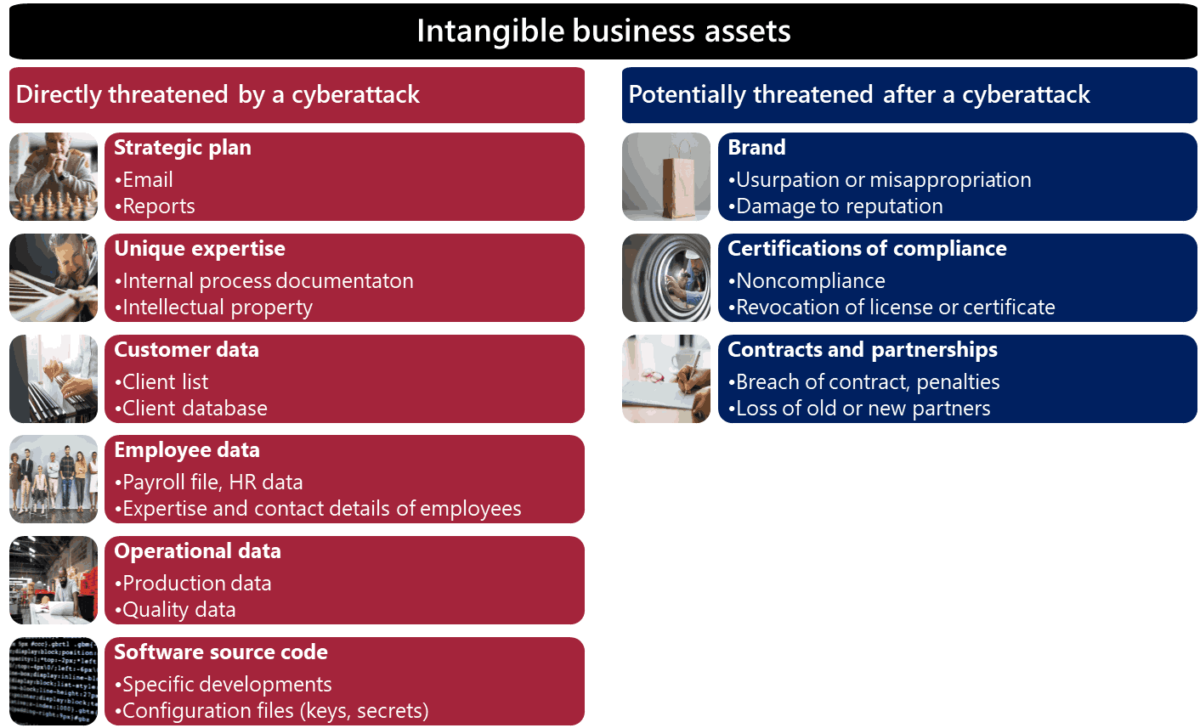
Once the classification is done, you can estimate the risk of each asset. The goal is to determine the likelihood and impact of an asset being destroyed or stolen, and then prioritize your efforts accordingly. Not all intangible assets have the same value, and some need to be highly protected. In addition to a comprehensive cybersecurity roadmap it’s crucial to implement specific measures for your most risky intangible assets.
The most valuable intangible assets should be protected by enhanced security measures: encryption of data at rest, strong internal authentication, immutable backup strategy.
Protecting your intangible assets requires a valuation approach that takes into account the unique needs of your business. By identifying and classifying your assets, estimating their risk and implementing specific measures to protect them, you ensure long-term success.